AWS Firewall Manager
In 2018, I wrote AWS firewall manager ( central management for your web application portfolio). This showed how multiple applications could be hosted, possibly across multiple AWS accounts or regions. It also demonstrated how to maintain central control over security settings and profiles. Firewall Manager supports multiple firewall types, just like Amazon Relational Database Service(RDS) supports multiple databases engines.
Cloud NGFW for AWS
Today, Firewall Manager now supports Palo Alto Networks Cloud Next-Generation Firewalls. Firewall Manager can be used to centrally provision and manage Cloud next-generation firewall resources. Also known as NGFWs, Firewall Manager can also monitor for non-compliant configurations across multiple accounts and Virtual Private Clouds. Cloud NGFW is a managed service that offers the best in-class security features. It’s also available as a native AWS experience with no hardware hassles and no software upgrades. While you are adding, changing, or removing AWS resources, your focus can be on keeping your organization secure and safe.
Palo Alto Networks was the first to implement deep packet inspection into their NGFWs. Cloud NGFW for AWS allows you to decrypt network packets and look inside. Then identify the applications using signatures and protocol decoding. This allows you to create fine-grained security management systems that are application-centric. It is much more efficient than simple models that are only based on IP addresses, ports, and protocols. Advanced URL filtering allows you to create rules that use curated sites (known as feeds), that distribute viruses, spyware and other malware. You also have many options for managing undesirable and desirable network traffic. Threat Prevention prevents known vulnerabilities, malware, and command/control communication.
You can choose the best deployment model for your network architecture with integration
Centralized – One firewall running in a centralized “inspection” VPC.
Distributed – Multiple firewalls, generally one for each VPC within the scope managed by Cloud NGFW for AWS.
Cloud NGFW protects outbound, inbound, and VPC-to-VPC traffic. We are launching with support for all traffic directions.
AWS Inside
Cloud NGFW is AWS’s centralized provisioning and management through Firewall Manager. It also makes use of other AWS features. Take, for example:
AWS Marketplace –AWS Marketplace offers the product in SaaS format. Pricing is based on firewall usage, traffic processed and security features used. Cloud NGFW for AWS can be deployed on a highly-available compute cluster that scales with traffic.
AWS Organizations – To identify and list new and existing AWS accounts, and to automate consistent cross-account deployment.
AWS Identity and Access Management (IAM) – To create cross-account Cloud NGFW roles to access log destinations in AWS Secrets manager.
AWS Config – To capture AWS resource changes such as VPCs and VPC route configurations.
AWS CloudFormation – To run , a StackSet which onboards every new AWS account through the creation of IAM roles.
Amazon S3, Amazon CloudWatch, Amazon Kinesis – Destinations for log files and records.
Gateway Load Balancer – To provide resiliency, scale, and availability for the NGFWs.
AWS Secrets Manager – To store SSL certificates in support of deep packet inspection.
Cloud NGFW for AWS Solutions
Before we get started on setting up our firewall, let’s go over some important concepts.
Tenant – A Cloud NGFW installation for AWS that is associated with an AWS customer accounts. Every purchase made from AWS Marketplace creates an additional tenant.
NGFW – A firewall resource that is used across multiple AWS availability zones and is dedicated to one VPC.
Rulestack – A set of rules that define the threat protections and access controls for one or more NGFWs.
Global Rulestack – An FMS policy is the representation of rules that apply to all NGFWs within an AWS Organization.
Using loud NGFW on AWS
Instead of the usual step-by, I will show you the highlights and how to set up the cloud ngfw for AWS. For more information, see Getting Started With Cloud NGFW for AWS.
I begin by visiting the NGFW Payas-You-Go listing on AWS Marketplace. I read the terms and click Continue to Subscribe.
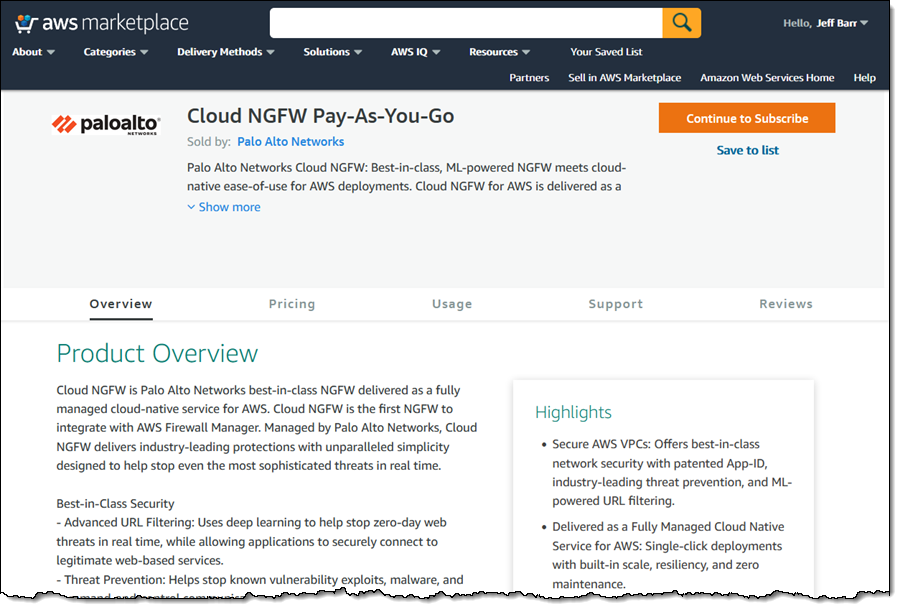


Cloud NGFW will send me temporary credentials to the Cloud NGFW console after I have subscribed. To log in, I use the credential. I then replace the temporary password by a long-term one.



Click Add AWS Account to enter my AWS account ID. The console will display my account as well as any other accounts that I have added.
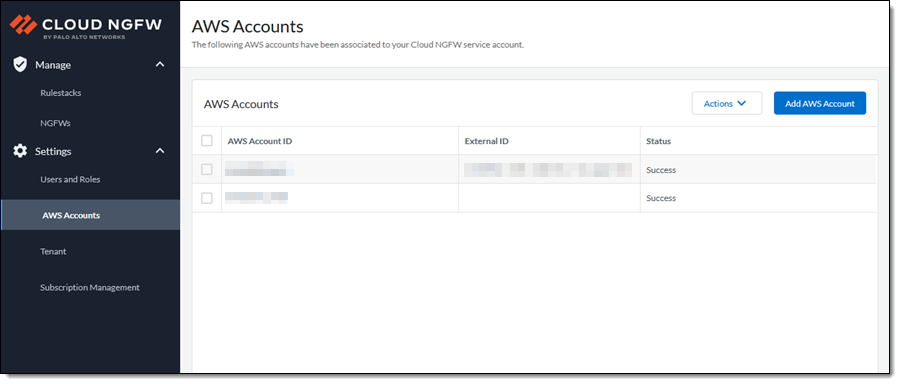


The NGFW console directs me to the AWS WebFormation console, where I am prompted to create a stack. This stack creates cross-account IAM role, designs (but not creates) logging destinations and allows Cloud NGFW to access certificates in Secrets Manager for packet encryption.
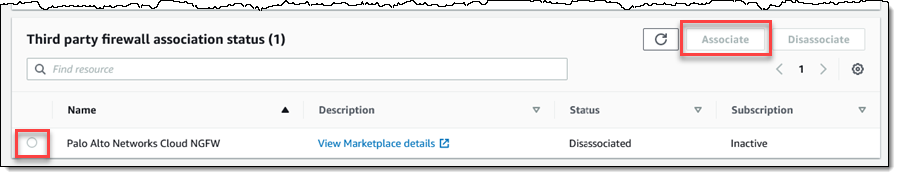
I click Settings to go to the AWS Firewall Manager console. My cloud NGFW tenant has been successfully associated with my account. Click the radio button beside the name of firewall. In this instance, it is Palo Alto Networks CloudNGFW. Next, click the Associate link. In a matter of minutes, the subscription status will change from Active to.
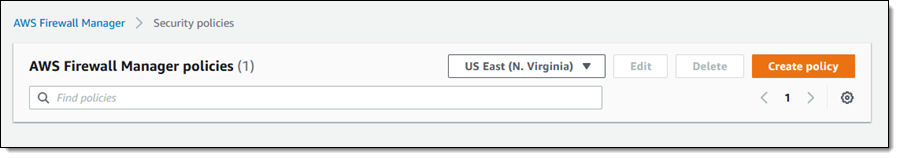
Once the NGFW tenant is associated with my account I return to the AWS Firewall Manager console and click Security policies to proceed. There are no policies yet, and I click Create policy to make one:


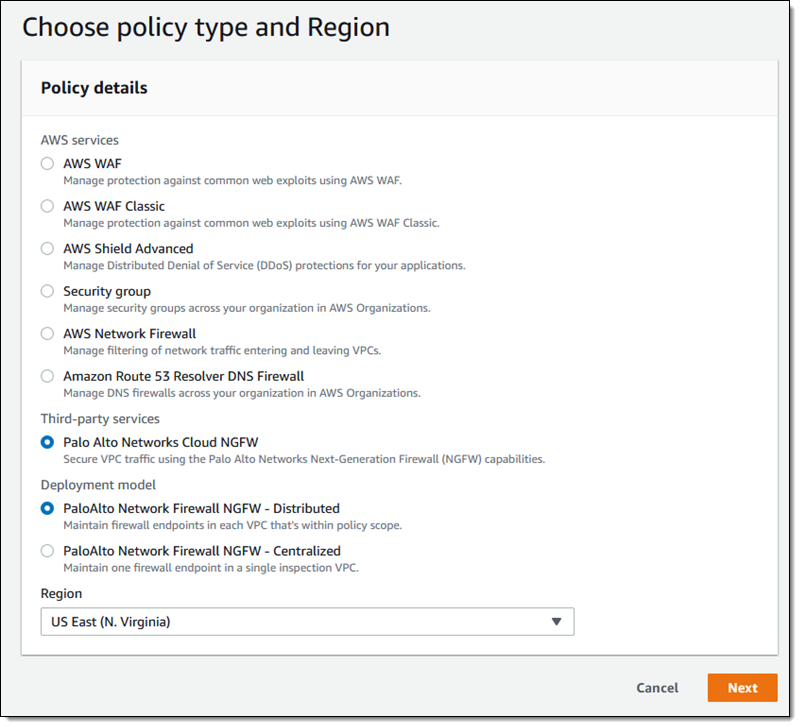


Enter a name for the policy ( Distributed-1) and choose one of the CloudNGFW firewall policies available to me. To navigate to Palo Alto Networks’ console, click Create firewall rule and follow the steps to create a new policy. Today, I choose grs-1
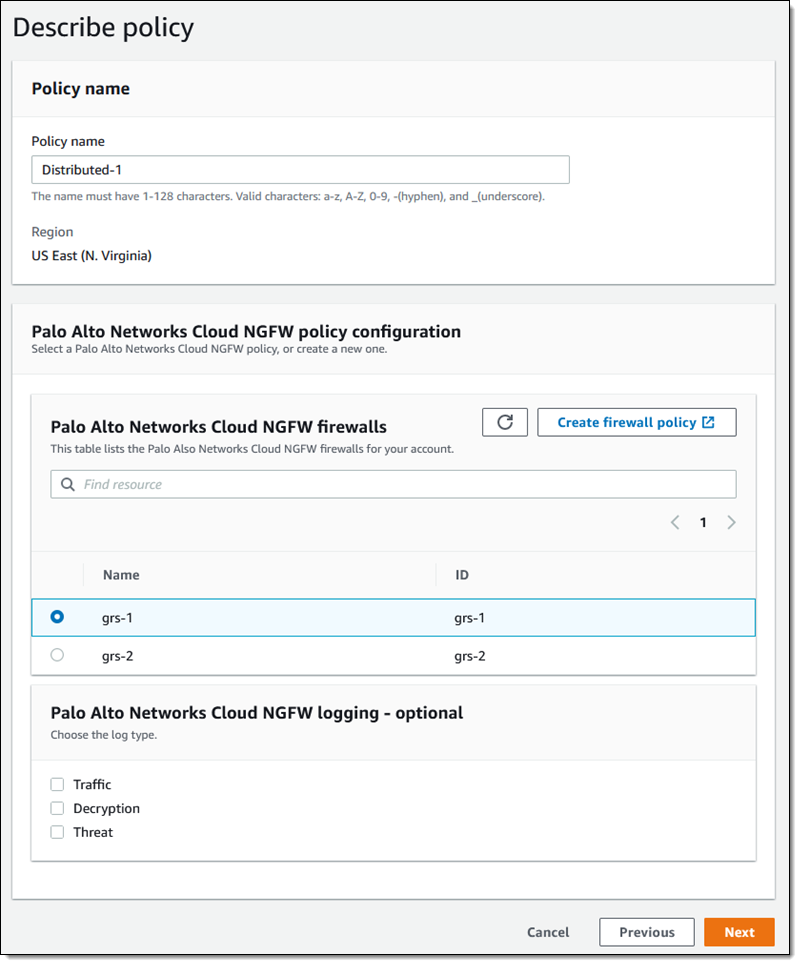


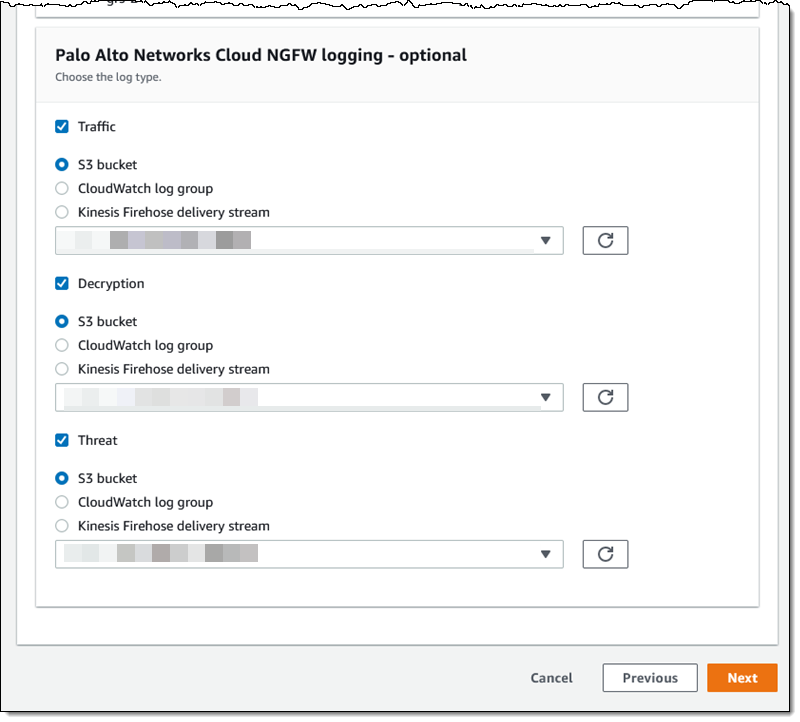
There are many options and choices when it comes to logging. Each of the three types (Traffic and Decryption) of logs can be routed to an S3 bucket or CloudWatch log group. Click on the S3 bucket. Next To continue:
Select the availability zones where I require endpoints. You can choose to pick by name or ID. I can also designate an optional CIDR block in each AZ which will be used for subnets.
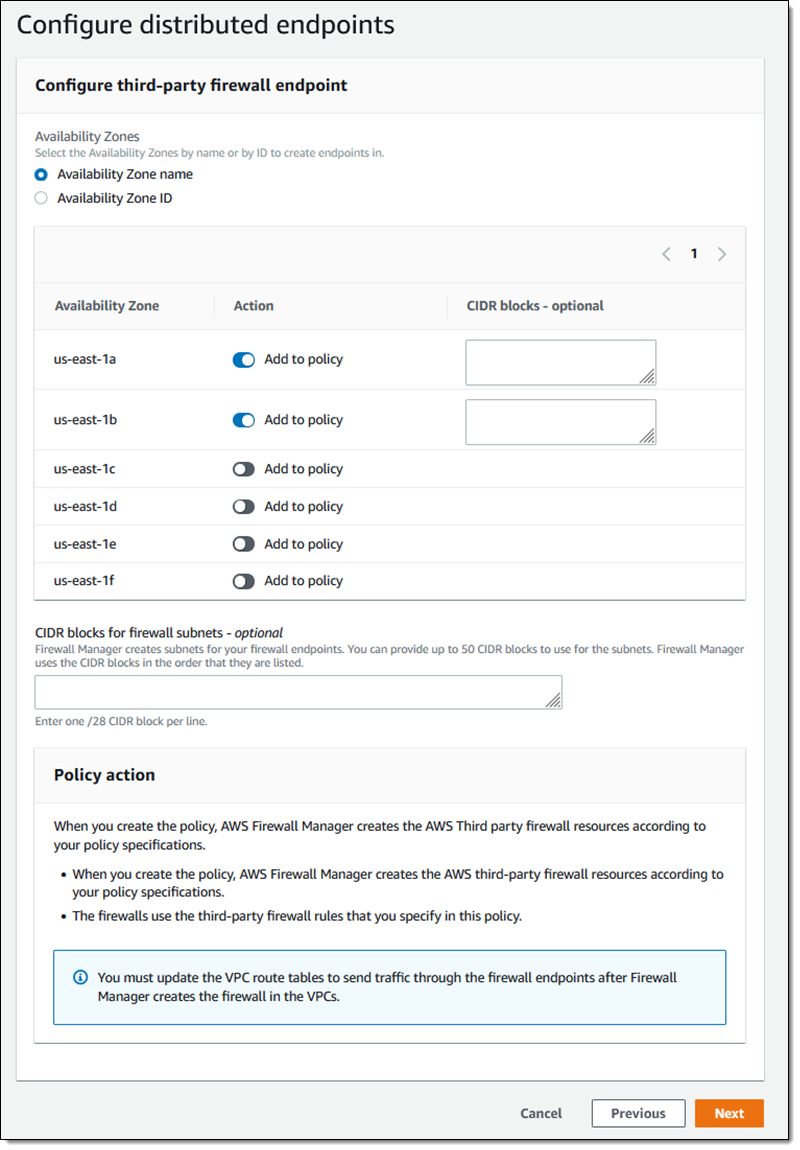


Next, you will need to decide the scope. This is the list of resources and accounts that will be covered by the policy. This feature is compatible with, as I mentioned earlier, AWS Organizations I have many options to choose from
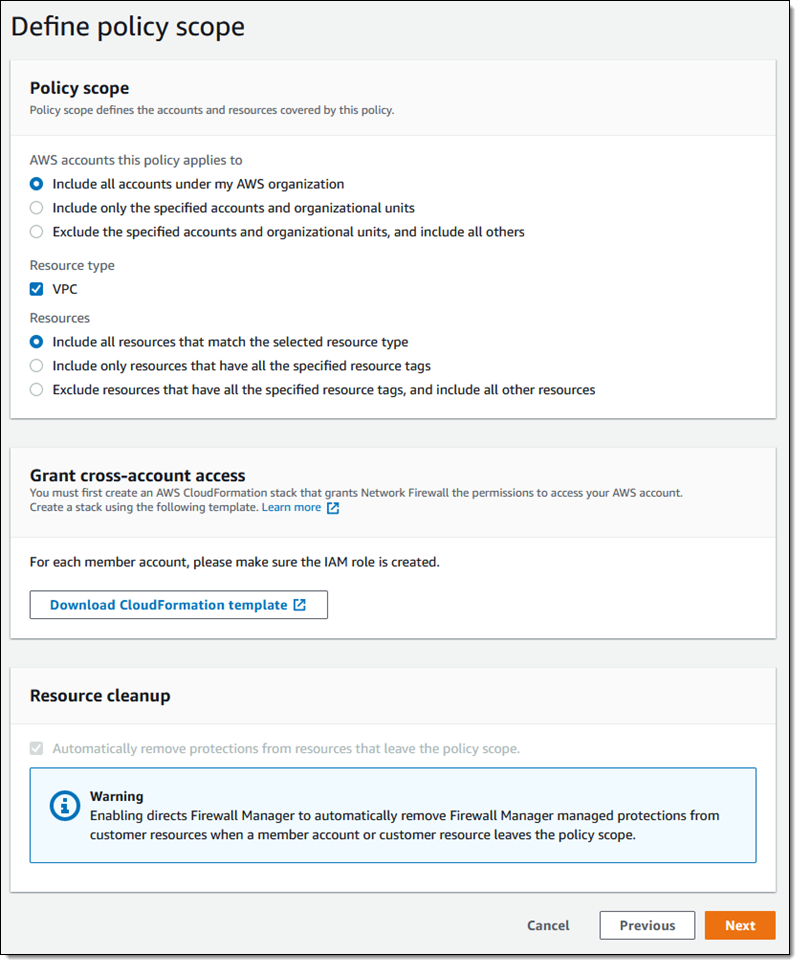


CloudFormation is used to create an IAM role for each member account. It will ask me to input the CloudNGFW account ID as well as the ExternalId parameters. Both of these parameters are accessible from the Palo Alto Networks console. You can tag your newly created policy on the next page:
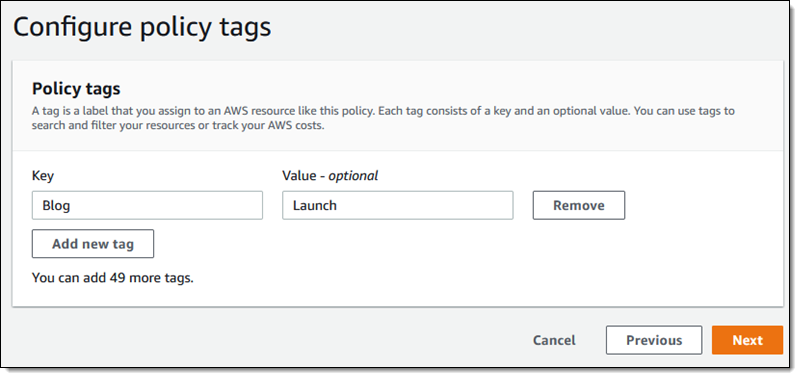


On the last page, I review and confirm my choices and then click Create policy.



My policy is immediately created and will begin listing the in-scope accounts in a matter of minutes. AWS Firewall Manager uses Cloud NGFW APIs under the hood to create NGFWs from VPCs within my in-scope account. The global rules are then automatically associated with the created NGFWs. AWS Firewall Manager creates NGFW endpoints within the subnets when the NGFWs can process traffic.
AWS Firewall Manager creates new NGFWs for my company as new AWS accounts are added to it.



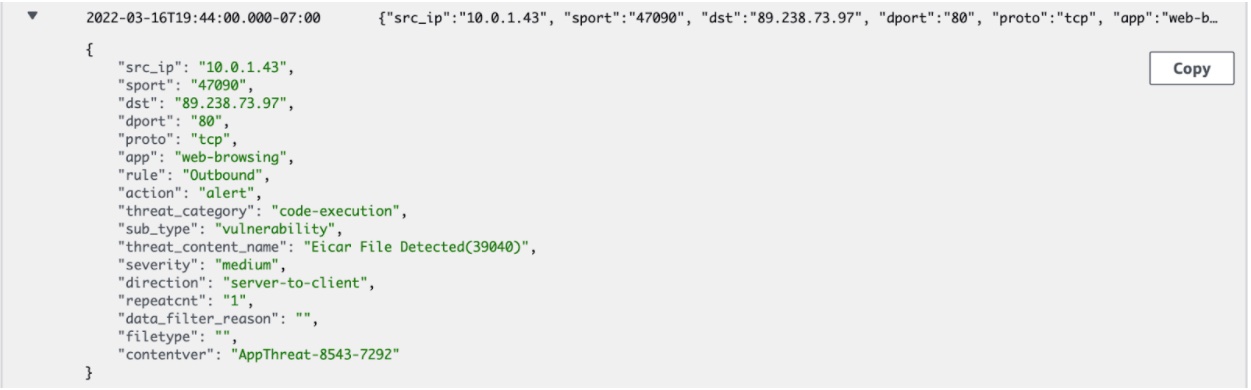
Next, I look at the Cloud NGFW threat logs in order to determine which threats are being blocked. Cloud NGFW protected this VPC from SIPVicious scanning.
Cloud NGFW also protected my VPC from malware downloads in this case:
Things to Know
AWS Firewall Manager as well as Cloud NGFW both are regional services. My AWS Firewall Manager policy therefore is regional. Cloud NGFW currently is available in the US East Region (N. Virginia) Regions and the US West Region (N. California), with plans for expansion in the near future.
AWS Firewall Manager



In 2018, I wrote AWS firewall manager ( central management for your web application portfolio). This showed how multiple applications could be hosted, possibly across multiple AWS accounts or regions. It also demonstrated how to maintain central control over security settings and profiles. Firewall Manager supports multiple firewall types, just like Amazon Relational Database Service(RDS) supports multiple databases engines.
Cloud NGFW for AWS
Today, Firewall Manager now supports Palo Alto Networks Cloud Next-Generation Firewalls. Firewall Manager can be used to centrally provision and manage Cloud next-generation firewall resources. Also known as NGFWs, Firewall Manager can also monitor for non-compliant configurations across multiple accounts and Virtual Private Clouds. Cloud NGFW is a managed service that offers the best in-class security features. It’s also available as a native AWS experience with no hardware hassles and no software upgrades. While you are adding, changing, or removing AWS resources, your focus can be on keeping your organization secure and safe.
Palo Alto Networks was the first to implement deep packet inspection into their NGFWs. Cloud NGFW for AWS allows you to decrypt network packets and look inside. Then identify the applications using signatures and protocol decoding. This allows you to create fine-grained security management systems that are application-centric. It is much more efficient than simple models that are only based on IP addresses, ports, and protocols. Advanced URL filtering allows you to create rules that use curated sites (known as feeds), that distribute viruses, spyware and other malware. You also have many options for managing undesirable and desirable network traffic. Threat Prevention prevents known vulnerabilities, malware, and command/control communication.
You can choose the best deployment model for your network architecture with integration
Centralized – One firewall running in a centralized “inspection” VPC.
Distributed – Multiple firewalls, generally one for each VPC within the scope managed by Cloud NGFW for AWS.
Cloud NGFW protects outbound, inbound, and VPC-to-VPC traffic. We are launching with support for all traffic directions.
AWS Inside
Cloud NGFW is AWS’s centralized provisioning and management through Firewall Manager. It also makes use of other AWS features. Take, for example:
AWS Marketplace –AWS Marketplace offers the product in SaaS format. Pricing is based on firewall usage, traffic processed and security features used. Cloud NGFW for AWS can be deployed on a highly-available compute cluster that scales with traffic.
AWS Organizations – To identify and list new and existing AWS accounts, and to automate consistent cross-account deployment.
AWS Identity and Access Management (IAM) – To create cross-account Cloud NGFW roles to access log destinations in AWS Secrets manager.
AWS Config – To capture AWS resource changes such as VPCs and VPC route configurations.
AWS CloudFormation – To run , a StackSet which onboards every new AWS account through the creation of IAM roles.
Amazon S3, Amazon CloudWatch, Amazon Kinesis – Destinations for log files and records.
Gateway Load Balancer – To provide resiliency, scale, and availability for the NGFWs.
AWS Secrets Manager – To store SSL certificates in support of deep packet inspection.
Cloud NGFW for AWS Solutions
Before we get started on setting up our firewall, let’s go over some important concepts.
Tenant – A Cloud NGFW installation for AWS that is associated with an AWS customer accounts. Every purchase made from AWS Marketplace creates an additional tenant.
NGFW – A firewall resource that is used across multiple AWS availability zones and is dedicated to one VPC.
Rulestack – A set of rules that define the threat protections and access controls for one or more NGFWs.
Global Rulestack – An FMS policy is the representation of rules that apply to all NGFWs within an AWS Organization.
Using loud NGFW on AWS
Instead of the usual step-by, I will show you the highlights and how to set up the cloud ngfw for AWS. For more information, see Getting Started With Cloud NGFW for AWS.
I begin by visiting the NGFW Payas-You-Go listing on AWS Marketplace. I read the terms and click Continue to Subscribe.



Cloud NGFW will send me temporary credentials to the Cloud NGFW console after I have subscribed. To log in, I use the credential. I then replace the temporary password by a long-term one.



Click Add AWS Account to enter my AWS account ID. The console will display my account as well as any other accounts that I have added.



The NGFW console directs me to the AWS WebFormation console, where I am prompted to create a stack. This stack creates cross-account IAM role, designs (but not creates) logging destinations and allows Cloud NGFW to access certificates in Secrets Manager for packet encryption.
I click Settings to go to the AWS Firewall Manager console. My cloud NGFW tenant has been successfully associated with my account. Click the radio button beside the name of firewall. In this instance, it is Palo Alto Networks CloudNGFW. Next, click the Associate link. In a matter of minutes, the subscription status will change from Active to.
Once the NGFW tenant is associated with my account I return to the AWS Firewall Manager console and click Security policies to proceed. There are no policies yet, and I click Create policy to make one:






Enter a name for the policy ( Distributed-1) and choose one of the CloudNGFW firewall policies available to me. To navigate to Palo Alto Networks’ console, click Create firewall rule and follow the steps to create a new policy. Today, I choose grs-1



There are many options and choices when it comes to logging. Each of the three types (Traffic and Decryption) of logs can be routed to an S3 bucket or CloudWatch log group. Click on the S3 bucket. Next To continue:
Select the availability zones where I require endpoints. You can choose to pick by name or ID. I can also designate an optional CIDR block in each AZ which will be used for subnets.



Next, you will need to decide the scope. This is the list of resources and accounts that will be covered by the policy. This feature is compatible with, as I mentioned earlier, AWS Organizations I have many options to choose from



CloudFormation is used to create an IAM role for each member account. It will ask me to input the CloudNGFW account ID as well as the ExternalId parameters. Both of these parameters are accessible from the Palo Alto Networks console. You can tag your newly created policy on the next page:



On the last page, I review and confirm my choices and then click Create policy.



My policy is immediately created and will begin listing the in-scope accounts in a matter of minutes. AWS Firewall Manager uses Cloud NGFW APIs under the hood to create NGFWs from VPCs within my in-scope account. The global rules are then automatically associated with the created NGFWs. AWS Firewall Manager creates NGFW endpoints within the subnets when the NGFWs can process traffic.
AWS Firewall Manager creates new NGFWs for my company as new AWS accounts are added to it.



Next, I look at the Cloud NGFW threat logs in order to determine which threats are being blocked. Cloud NGFW protected this VPC from SIPVicious scanning.
Cloud NGFW also protected my VPC from malware downloads in this case:
Things to Know
AWS Firewall Manager as well as Cloud NGFW both are regional services. My AWS Firewall Manager policy therefore is regional. Cloud NGFW currently is available in the US East Region (N. Virginia) Regions and the US West Region (N. California), with plans for expansion in the near future.